[JAVA] What is Keycloak
Introduction
Suddenly, this time, a volunteer member of NRI OpenStandia will be writing an advent calendar for Keycloak. In the last 25 days, I would like to tell you about the features of Keycloak, what you can understand by actually touching it, and Keycloak's efforts at NRI OpenStandia.
Why Keycloak?
Keycloak is an open source identity access management software. It realizes single sign-on and API access authentication / authorization control, and is one of the latecomers in this field of software. Community-based development is currently underway and is said to be one of the most dynamic software in the field. Thoutht Works' Technology Radar, a well-known source of technology trends, also made its name for the first time this March (March 2017). Also, in the latest version just the other day, the evaluation has changed from ASSESS to TRIAL, and it is getting more and more attention.
https://www.thoughtworks.com/radar/platforms/keycloak

What is the degree of attention in the world and Japan?
For reference, I looked at the attention level of the last 5 years on Google Trends. (Compared to OpenAM, which has recently shifted to commercial-based handling)
■ OpenAM v.s. Keycloak worldwide, 5-year version
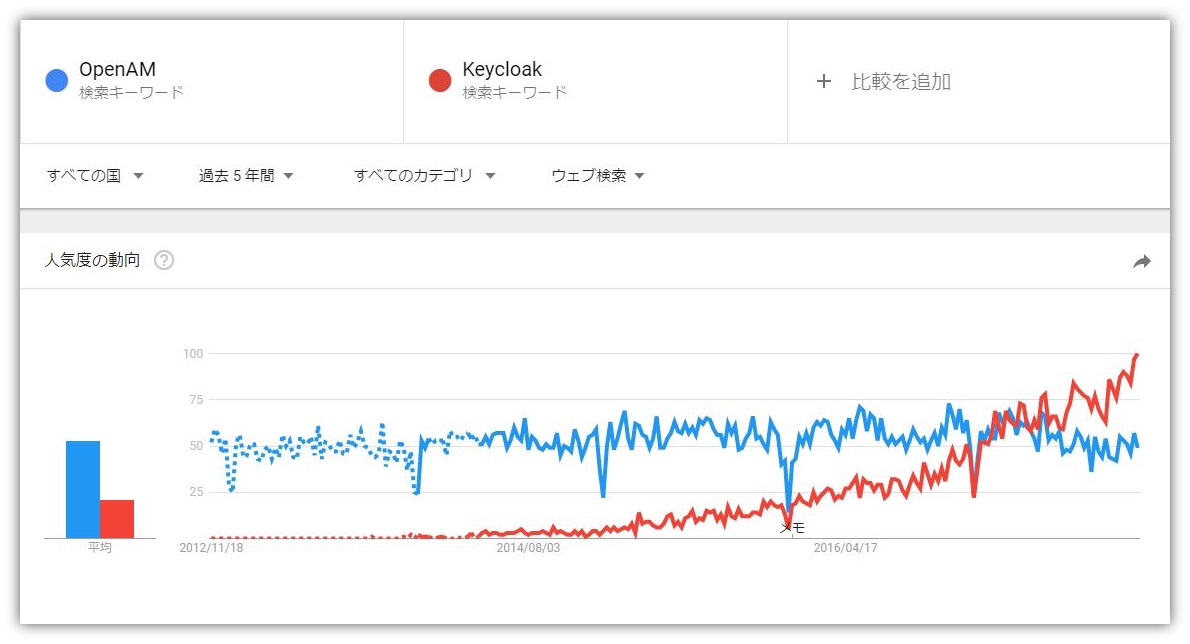
■ OpenAM v.s. Keycloak Japan, 5-year version
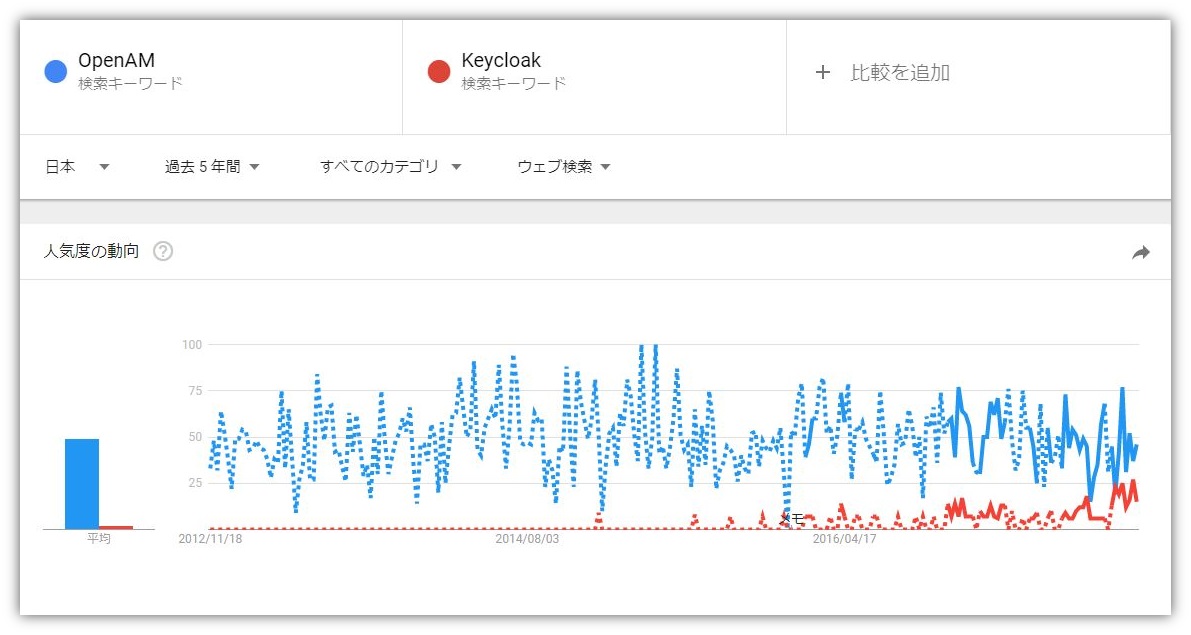
While it is gaining worldwide attention, it seems that it is not yet widespread in Japan. NRI also hopes to contribute to the excitement of Keycloak in Japan.
: point_up_2: NRI will continue to handle ForgeRock OpenAM as before. ForgeRock is an undisputed market leader in this field, with one outstanding feature and track record. We believe that it is necessary to use them properly according to the customer's requirements.
Efforts of other companies
Hitachi, Ltd. is famous as a company that disseminates information related to Keycloak in Japan. Please refer to the @IT article below for information. http://www.atmarkit.co.jp/ait/articles/1708/31/news011.html
Features provided by Keycloak
Function in Server Admin (Japanese version) of Keycloak documentation Since there is a description about, I will quote from there.
- Single sign-on and single sign-out for browser applications.
- Support for OpenID Connect.
- Support for OAuth 2.0.
- SAML support.
- Identity Brokering-Authentication by an external OpenID Connect or SAML-enabled identity provider.
- Social Login-Login via Google, GitHub, Facebook, Twitter and other social networks.
- User Federation-User synchronization from LDAP or Active Directory.
- Cerberus integration-Authentication integration for users who have logged in to the Cerberus server.
- A management console for centralized management of users, roles, role mappings, clients and settings.
- An account management console that allows users to centrally manage their accounts.
- Theme support-Customize all user screens and integrate application and branding.
- Two-factor authentication-TOTP / HOTP support using Google Authenticator and FreeOTP.
- Login Flow-Optional user self-registration, password recovery, email verification, forced password change, etc.
- Session management-Administrators and users can view and manage their own sessions.
- Token Mapper-Specify how user attributes, roles, etc. are reflected in tokens and statements.
- Per-realm, application, and user-based Not-before revolving policies.
- CORS support-CORS-enabled client adapters.
- Service Provider Interface (SPI)-Numerous SPIs for customizing various aspects of the server. Authentication flows, user federation providers, protocol mappers and much more.
- Client adapters such as JavaScript, WildFly, JBoss EAP, Fuse, Tomcat, Jetty, Spring.
- Support for any platform / language with the OpenID Connect resource provider library or the SAML 2.0 service provider library.
I think I can introduce some details in this Keycloak by OpenStandia Advent Calendar 2017. Please look forward to it!
Keycloak license
Keycloak is distributed under the Apache 2.0 license. Since the source code can be freely modified and released on condition that the usage license is clearly stated, it is easy to use it by incorporating it into your own product.
Function comparison with OpenAM
Let's compare it with OpenAM, which is a representative product of SSO, with a little more detailed functions.
| category | function | Keycloak | OpenAM |
|---|---|---|---|
| Authentication | 多要素Authentication | ○ | ○ |
| OTP | ○ | ○ | |
| Risk-based authentication | ☓ | ○ | |
| Desktop SSO | ○ | ○ | |
| External IdP authentication | ○ | ○ | |
| Proxy authentication | ☓ | ○※1 | |
| Authorization | User attribute access control | △※2 | ○ |
| Role-based access control | △※2 | ○ | |
| Other access control (URL, IP address, time zone, etc.) | △※2 | ○ | |
| self-service | account registration | ○ | ○ |
| Password reset | ○ | ○ | |
| User attribute management | ○ | ○ | |
| Agent/Client adapter | Supported platforms | Few | Many |
| Other | Support for standard protocols(SAML2.0/OIDC1.0/OAuth2.0) | ○ | ○ |
| Support for legacy standard protocols(SAML1.x/WS-Federation etc.) | ☓ | ○ | |
| Code base | small | Huge | |
| open/closed | open | バージョン13系まではopen、以降は最新版はclosed |
-
- 1 Realized in combination with OpenIG, which is a peripheral product of OpenAM.
-
- 2 The commercial version of Keycloak Red Hat Single Sign-On (RH SSO) is still treated as a Technology Preview.
Looking at it like this, in terms of functionality, OpenAM is overwhelming with ○. To be honest, it is still inferior to OpenAM in terms of functionality, but since it is new software with less clinging to the past, the code base is small and it is easy to maintain.
Unfortunately, it was closed after version 13 of OpenAM at the end of last year (the latest version will be released as OSS about two years after its release). Therefore, when it comes to ** OSS ** SSO products, I think Keycloak will be a strong candidate in the future. In fact, Keycloak is already running in production at our company, but it works very stably: smile:
By the way, our @wadahiro announced a use case at the OSS Security Technology Association 2nd Study Group held the other day. So, please refer to that Material.
Keycloak features
In Keycloak, in addition to the main body SAML2.0 / OAuth2.0 / OIDC authentication authorization server, ** client adapter ** is distributed. The client adapter is equivalent to an agent in OpenAM, and is used by incorporating it into an application or application server subject to SSO protection. This is the so-called SSO method, which is often called the agent method. The client adapter talks to the Keycloak server using the standard protocol instead of the application, and realizes SSO.
There are two large client adapters, one for OpenID Connect and one for SAML 2.0. Below is a list of supported platforms and their versions (as of Keycloak 3.4.0.Final).
For OpenID Connect
| Supported platforms | Corresponding version |
|---|---|
| Keycloak Proxy | - |
| WildFly | 10, 9, 8 |
| JBoss EAP | 7, 6 |
| JBoss AS | 7.1 |
| JBoss Fuse | 6.2, 6.3 |
| JavaScript | - |
| Jetty | 9.4, 9.3, 9.2, 9.1, 8.1 |
| Tomcat | 8, 7, 6 |
For SAML 2.0
| Supported platforms | Corresponding version |
|---|---|
| WildFly | 10, 9 |
| JBoss EAP | 7, 6 |
| JBoss AS | 7.1 |
| Jetty | 9.4, 9.3, 9.2, 8.1 |
| Tomcat | 8, 7, 6 |
One of the more special adapters is the Keycloak Proxy. This is a reverse proxy that operates independently and performs reverse proxy type SSO. The details will be written by @yagiaoskywalker on the 7th day, so please read that as well.
In addition, I want to SSO applications other than the above supported platforms with Keycloak! At that time, don't worry. Keycloak supports standard protocols (or can only speak), so if your application supports SAML 2.0 or OpenID Connect, you can easily SSO. If it is a package software or cloud service of a famous place, I think that there are many places that support SAML 2.0 or OpenID Connect. Even for scratch development applications, modern frameworks and libraries should be relatively easy to support SAML 2.0 or OpenID Connect.
On the other hand, when it comes to supporting existing applications, you may often want to reduce the scope of modification by reducing the scope of impact. In such a case, a reverse proxy type SSO method that performs SSO by setting up a reverse proxy server in front of the application may be better. In this case, if the application is slightly modified to authenticate with the user ID linked in the HTTP header of the request, it will be possible to support SSO.
In addition to Keycloak Proxy provided by Keycloak, there are several proxy servers that support SAML2.0 / OpenID Connect in OSS to realize reverse proxy type SSO. There is mod_auth_openidc for Apache as a typical one that we often use, but @yagiaoskywalker will write it on the 8th day as well. Please stay tuned!
Advent calendar writing members
Finally, I would like to introduce the members who will write (plan) the Advent calendar in the last 25 days. On Qiita, there are people who want to go only by handle name, so here we will introduce it based on handle name!
| Handle name | Self-introduction |
|---|---|
| @daian183 | I recently managed Keycloak's external sales and internal members, etc. |
| @wadahiro | Open Standia's proud technical evangelist(I like all directions) |
| @tamura__246 | Open Standia's proud technical evangelist(I like OpenAM) |
| @kabao | Open Standia's proud technical evangelist(DB lover) |
| @mamomamo | A young leader who is active in both support and SI |
| @izey0306 | Young members who are active in both support and SI |
| @yoonis | SSO/IDM project experience, Keycloak verification(In our company)Main members of |
| @naokiiiii | SSO/IDM project experience, Keycloak verification(In our company)Leading leader |
| @rawr | An amazing person who can do anything quickly while complaining from the application to the base |
| @katakura__pro | SI carried out by OpenStandia/support/A leader who handles a wide range of tasks such as maintenance |
| @masuo3 | Engineers and leaders who can do anything regardless of product |
| @yagiaoskywalker | From OpenStandia's proud support craftsman, SSO related products to recently IDM related products |
| @rkato | OpenStandia's Sapporo unit, get an article written from Sapporo |
In addition, this time, I will write articles mainly for members of NRI OpenStandia, but Hitachi will also participate! It is scheduled to appear around the 20th day, so please look forward to it.
Well then, thank you for 25 days!
Recommended Posts